Today my fellow SEO, Sander Tamaëla pointed out on Twitter that the popular Chrome extension Webpage Screenshot (4 million downloads according to their website) is sending all kinds of data to their servers, like the visited pages, session IDs, social connections etcetera:
Webpage Screenshot extension voor Chrome: dat ding post allerlei info naar zijn servers, oa: sessie ID’s,bezochte pagina,social connections
— Sander Tamaëla (@tamaela) 5 augustus 2014
This made me curious, since I was aware of the possibilities of tracking people’s behaviour by browsers add-ons like toolbars and extensions but I never heard anyone about a popular Chrome extensions. I’m not that paranoia and mostly aware of what I’m doing online, but I wanted to know how Google Chrome is dealing with plugin acception and how it communicates about these permissions given once you install an extension.
I ended up with this PDF document of the NSA (who else would you trust on this subject!) about Deploying and Securing Google
Chrome in a Windows Enterprise which explains all the possibilites in detail. To sum it up, Google divides the extensions into three main categories:
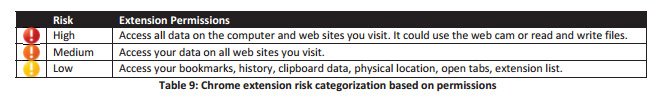
Read that first line again: extensions categorized as High Risk, have access to all data on your computer and all the websites you visit. Google has included some explanation in their support section as well: Permissions requested by apps and extensions. Extensions categorized as “Medium Risk” have the following access: “This item can read every page that you visit — your bank, your web email, your Facebook page, and so on. Often, this kind of item needs to see all pages so that it can perform a limited task such as looking for RSS feeds that you might want to subscribe to.”
The NSA shares an example of an extension categorized as high risk, developed by Google:

As you can see, once you select an extensions before installing, it shows the permission level you will comply to once you install the plugin. The NSA document is dated October 2012, and currently, this is not shown at all in the extensions screen before installing:

So so think the extension is looking good, got positive reviews, there are no elements on that screen that could change your mind about installing a new extensions. You click on the “Free” button and you get the following confirmation screen:

But you already read all the information on the screen that suits that purpose best, all your mates are using the plugin and installing this was recommended by all the well known SEO ninja’s on the planet. Most people won’t read, let alone think, about the fact you are giving the extensions access to all your browsing data. I’m not going into detail about what you can do when you have access to this data, but most important for most people is their privacy, next to your clients privacy when working as a search engine optimizer. I’m always using incognito mode, without any extensions active, to do most of my personal browsing (banking, social media, shopping) but for most SEO related work I use the standard mode so I can use all my extensions without to much hassle.
Update 06-08: I decided to dig a bit more into the working of extensions. Every extension requires a manifest.json file, to be working. In that JSON file, the required permissions are listed. These files can be found in the folder with all extensions. In Windows these extensions can be found in the following folder: C:\Documents and Settings\*UserName*\Local Settings\Application Data\Google\Chrome\User Data\Default\Extensions or C:\Users\*UserName*\AppData\Local\Google\Chrome\User Data\Default\Extensions An example from the Ayima Redirect Path extension:
"manifest_version": 2,
"minimum_chrome_version": "17",
"name": "Redirect Path",
"permissions": [ "tabs", "webRequest", "\u003Call_urls\u003E", "cookies" ],
"update_url": "https://clients2.google.com/service/update2/crx",
"version": "0.7.2"
So the required permissions are clearly visible. Google listed all the permissions possible with an extensive explanation about the working of each API that is used once granted access.
Which SEO extensions share your data?
To see which plugins have access to all my browsing activities I checked the most commonly used SEO extensions. For a detailed view, download the PDF so you can see the access required per extensions or hover the green, orange and red icons.
| Company / Developer | Extension | Users | Alert | |
| Evernote | ExtensieEvernote Web Clipper | 3.391.053 |  |
|
| Getpocket | Save to Pocket | 1.682.831 |  |
|
| Glenn Wilson | User-Agent Switcher for Chrome | 578.029 |  |
|
| editthiscookie.com | EditThisCookie | 442.200 |  |
|
| ExtensionPageSpeed Insights (by Google) | 400.690 |  |
||
| Alexa | Alexa Traffic Rank | 338.961 |  |
|
| Chromefans.org | PageRank Status | 314.665 |  |
|
| Rapportive.com | Rapportive | 308.332 |  |
|
| Bitly.com | Bitly | 285.036 |  |
|
| seoquake.com | SEOquake | 191.707 |  |
|
| marketingabuse.com | SEO for Chrome | 155.399 |  |
|
| Moz | Mozbar | 137.282 |  |
|
| benblack86 | Linkclump | 99.750 |  |
|
| WooRank | SEO & Website Analysis | 87.885 |  |
|
| builtwith.com | BuiltWith Technology Profiler | 80.979 |  |
|
| cartercole.com | SEO Site Tools | 73.844 |  |
|
| Omiod.com | SEO SERP Workbench | 66.376 |  |
|
| Paul Livingstone | Check My Links | 65.668 |  |
|
| webrankstats.com | WebRank SEO | 55.459 |  |
|
| mnmldave.github.io | Scraper | 53.305 |  |
|
| Omiod.com | META SEO inspector | 40.957 |  |
|
| esolutions.se | Live HTTP Headers | 39.784 |  |
|
| Majestic | Majestic SEO Backlink Analyzer | 33.101 |  |
|
| Redflymarketing.com | SEO Global For Google Search™ | 24.970 |  |
|
| igorware.com | NoFollow | 21.767 |  |
|
| Ayima | Redirect Path | 20.807 |  |
|
| Vincent Paré | Copy All Urls | 17.376 | Extremely  |
|
| quickwin.co.il | Google Analytics URL Builder | 11.515 |  |
|
| samdutton.com | Page speed test | 8.877 |  |
|
| Sellhack.com | Sellhack | 8.155 |  |
|
| www.eisbahn.jp/yoichiro | Semantic Inspector | 7.589 |  |
|
| reliablesoft.net | Reliablesoft – SEO Tips | 6.592 |  |
|
| pagenoare | Link grabber | 4.204 |  |
|
| wordtracker.com | Wordtracker Scout | 3.616 |  |
|
| monitorbacklinks.com | Monitor Backlinks | 3.447 |  |
|
| dejanseo.com.au | SERP Preview Tool | 3.079 |  |
|
| Tomas Balciunas | SiteCatalyst Debugger | 2.717 |  |
|
| Fat Joe | Fat Rank | 2.573 |  |
|
| Buzzstream | BuzzStream Buzzmarker | 2.222 |  |
|
| AKM3 | Seerobots | 1.899 |  |
|
| j832.com | Canonical | 1.885 |  |
|
| SiteTrail | SiteTrail | 1.806 |  |
|
| bulkseotools.com | Bulk SEO Tools | 1.050 |  |
|
| seoprofiler.com | SP Backlink Manager | 559 |  |
I can imagine some tools need access to some browser sources, but I would like extension publisher to be more clear about what they are using and why they need specific access per extension. Next time read the TOS and make sure you know what you are installing in your browser 🙂
Leave a Reply